Development Environments
You can work on this assignment in Virginia cyber range or on the CS winsrv01.cs.virginia.edu (server). Login with Remote Desktop.
Windows Remote Desktop App is installed by default. You can can download windows Remote Desktop client for MAC here. https://install.appcenter.ms/orgs/rdmacios-k2vy/apps/microsoft-remote-desktop-for-mac/distribution_groups/all-users-of-microsoft-remote-desktop-for-mac
username: csdom\yourcsusername
password: yourcspassword
Overview
This assignment is a Hacking Challenge designed to test your skills in binary analysis, fuzzing, and exploit development. Carefully follow the instructions below and submit your responses according to the guidelines. If you have questions or need guidance, I’ll be available to provide help, hints, and feedback during class time.
Hacking Challenge Instructions
2. Exploit Development and Metasploit Module
- Setup:
- Download and install the Sync Breeze (Sync Breeze Vulnerable Application) application on your Windows Desktop
- Update the Windows firewall rules to allow connections from your Kali machine. to Sync Breeze app. (normal)
- Enable Web-login by going to Tools, Advanced, Server.
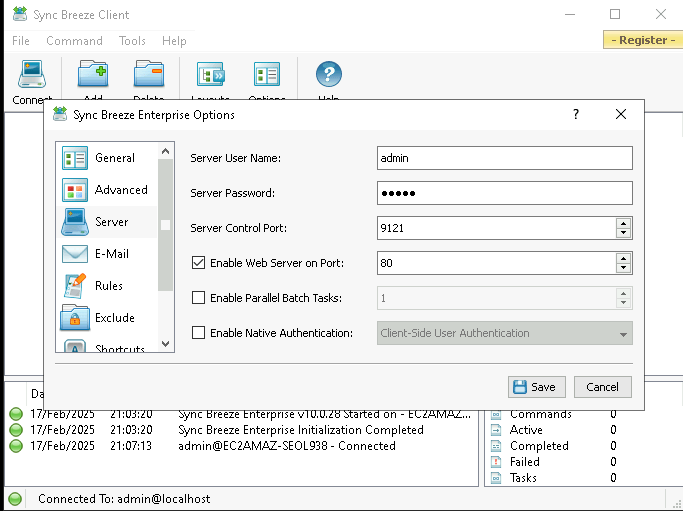
- Test your setup to confirm you can log into the application from Kali.
- Disable Windows Protections:
- Disable DEP (Data Execution Prevention):
- Navigate to Advanced System Settings -> Performance Settings -> Turn on DEP for essential Windows programs and services only.
- We will do this manually but you can also write ROP chains to disable DEP
- Navigate to Advanced System Settings -> Performance Settings -> Turn on DEP for essential Windows programs and services only.
- Disable DEP (Data Execution Prevention):
- Discover and Exploit a Vulnerability:
- Use fuzzing techniques to analyze the Sync Breeze Vulnerable Application. Focus on identifying vulnerabilities in the login page or other exposed functionality.
- Provide screenshots of how you discovered the vulnerability. It O.K to look up exploit code on searchsploit. But Provide screenshots and write on you discovered the vulnerability. You have everything you need to be able to discover a vulnerability like this on your own. (Hint: fuzz the password field, note there is a public exploit for username field: https://www.exploit-db.com/exploits/42928 )
- Once you identify a vulnerability:
- Write a Metasploit module to exploit it.
- Submit a screen short of:
- The resulting shell session running on the target machine.
- Use fuzzing techniques to analyze the Sync Breeze Vulnerable Application. Focus on identifying vulnerabilities in the login page or other exposed functionality.
- Hints:
- Refer to the attached chapter from the Metasploit book for guidance on fuzzing and exploit development. The chapter includes examples and techniques similar to what you’ll encounter in this challenge.
- I’m happy to provide further hints or assistance during class or office hours if you need.
Deliverables
- Metasploit Module:
- Submit your fully developed Metasploit module.
- Include a screenshot showing a working shell session obtained via your exploit.
- Screen shot of showing that you override the return return address and jumping debug_trap.
- Provide screenshots showing how you used fuzzing to discover the lengths of injection.
Resources
- Download the vulnerable Sync Breeze application here:
Sync Breeze Vulnerable Application - Refer to the attached Metasploit (Chapter 14 Metasploit 2nd Edition) guide for help with fuzzing and exploit development.
Submission Guidelines
- Upload all files, including:
- The discovered passcode or your approach description for the binary challenge.
- The developed Metasploit module.
- Screenshots and a screen recording as specified in the instructions.
- Submit all materials via the designated platform or email by the due date.